CYBER EMERGENCY MANAGEMENT
by zeroBS.
„The goal of CEM is to rethink what already exists and thus strengthen the resilience of the organization.“

Challenge
The implementation of separated organizational and technical security measures can no longer effectively combat today’s complex cyber- attacks.
These measures are often divided into different areas and responsibilities.
One area takes care of information security, another of IT emergency management, another of crisis management and business continuity, another of technical security measures and everyone sees only their own area of responsibility and defines their own goals independently of each other and independent from the business goals.
This means that the comprehensive and close cooperation between the technical and organizational departments involved and external service providers and their central control, which is necessary to effectively combat a cyber- attack, is not possible.
This results in significant deficiencies in the cyber security architecture of companies, which can lead to considerable damage and do not adequately implement the new compliance requirements, such as DORA, NIS2 or TISAX VDA-ISA 6.
The challenges in the cyber security environment require a general rethinking away from classic solution approaches.
Focused on cyber threats, modern through the application of current standards and best practice, modular through defined products and processes and effective through structured and modern processes, this is defined by CYBER EMERGENCY MANAGEMENT.
Solution
CYBER EMERGENCY MANAGEMENT is a combination of security incident, incident response, emergency, and crisis management.
It is focuses on cyber threat situations, is modern by applying current standards and best practice and is modular through defined products and processes.
CYBER EMERGENCY MANAGEMENT leads to a functioning and effective cyber defense, implementing only necessary but effective defense measures and thereby reducing the organization’s costs for implementation as well as for possible damage.
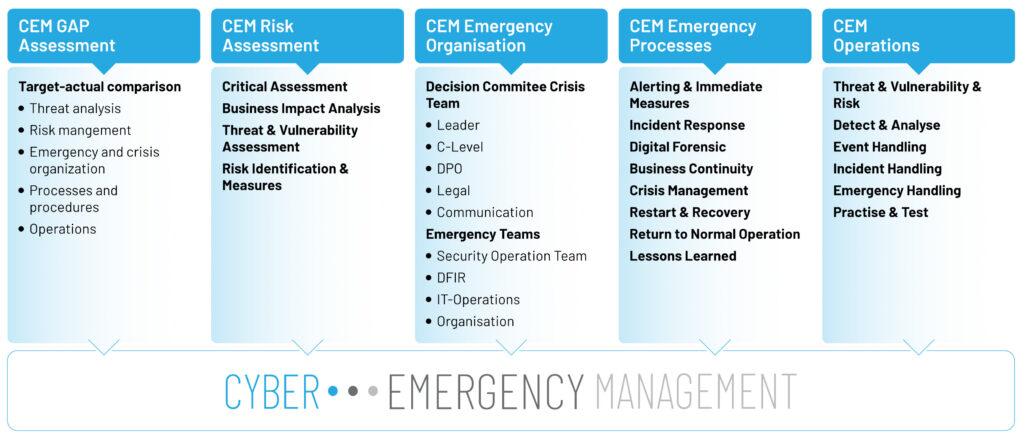
KEY COMPONENTS OF CYBER MANAGEMENT
1. GAP Assessment
Identify the maturity level of processes and procedures required for implementation.
2. CEM Risk Assessment
Identify critical assets, threats & vulnerabilities the resulting risks and measures.
3. CEM Emergency Organization
Defines an effective crisis organization.
4. CEM Emergency Process
Establish a strong combination of crisis-, emergency and incident response process.
5. CEM Operations
Defines strategies, plans, and measures to effectively manage and mitigate the impact of cyber incidents.
CYBER EMERGENCY MANAGEMENT encompasses a comprehensive approach:
– deal with cyber threats
– aiming to enhance an organization’s resilience
– ability to respond to and recover from cyber incidents
It involves a combination of preparedness, response, recovery, mitigation, and coordination efforts to address the dynamic and evolving nature of cyber threats.
Products and Work Packages
Standards & Best Practice
CEM consists of components of the following standards and best practice:
ISO / IEC 27035, ISO / IEC 27037, NIST SP 800, MITRE ATT&CK, MITRE DEFEND, TRAM, FAST, CVE, CAPEC, NVD, GuardSight
Conclusion
The CYBER EMERGENCY MANAGEMENT process model allows implementation in any organization, regardless of the status quo.
It checks and evaluates existing processes and models them in his special process model.
It is also able to work with external security services, such as an external SoC or DFIR services, and actively integrate them into its processes.
The goal of CEM is to rethink what already exists and thus strengthen the resilience of the organization.