DDoS-Stresstest
by zeroBS.
Highest level of expertise in DDoS testing and consulting.
IT-Security made in Germany (since 2015)
Partner DDoS Resiliency Score (DRS)
Introduction
zeroBS is a pioneer in the field of IT security and offers a dedicated, cloud-based platform that has been specially developed for carrying out DDoS stress tests. Further core competences are in the simulation of network attacks and the testing of protection mechanisms for your infrastructure.
Our customisable platform enables targeted testing in the form of Layer 7 attacks and IPv6 protocols. We evaluate the resilience of your systems from various entry points such as existing anti-DDoS appliances, firewalls, load balancers, application servers - including BGP-side entry points.Features
- Volume attacks up to 100 GB/s or 100 million pps via TCP, UDP or ICMP
- Layer 7 attacks with full-stack browsers, up to 10 million RPS
- 50 locations, up to 100,000 IPs possible
- IPv4 and IPv6
- Automated setup and orchestration of the infrastructure
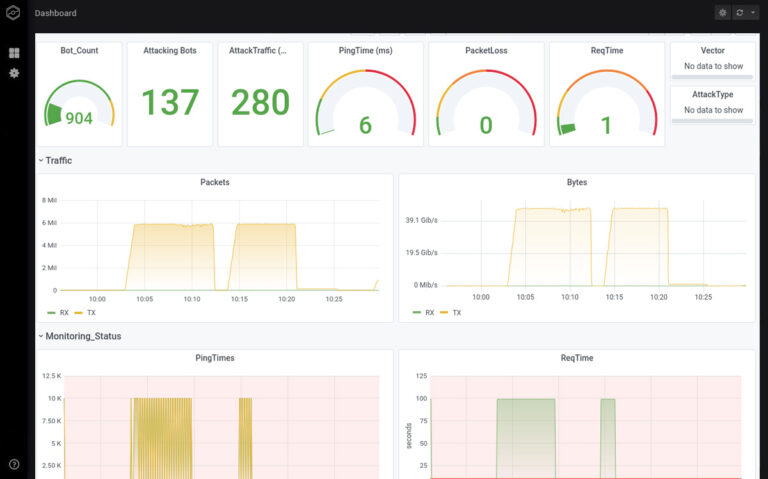
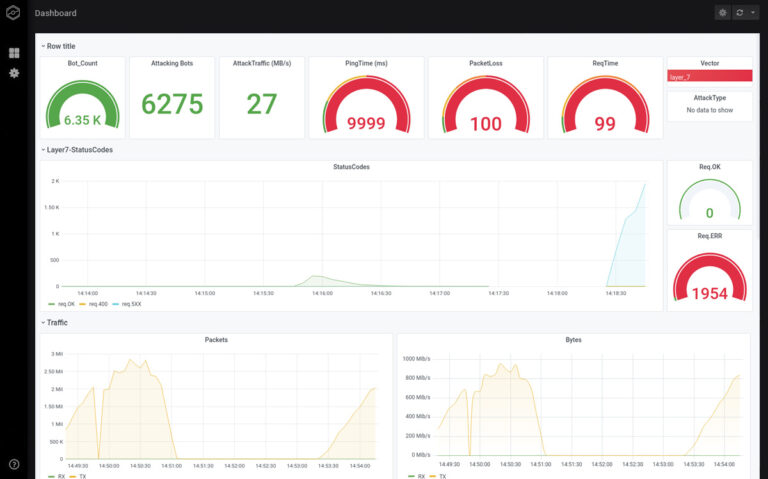
- Dashboard and Monitoring
- Exports and logs for easy tracking and analysis
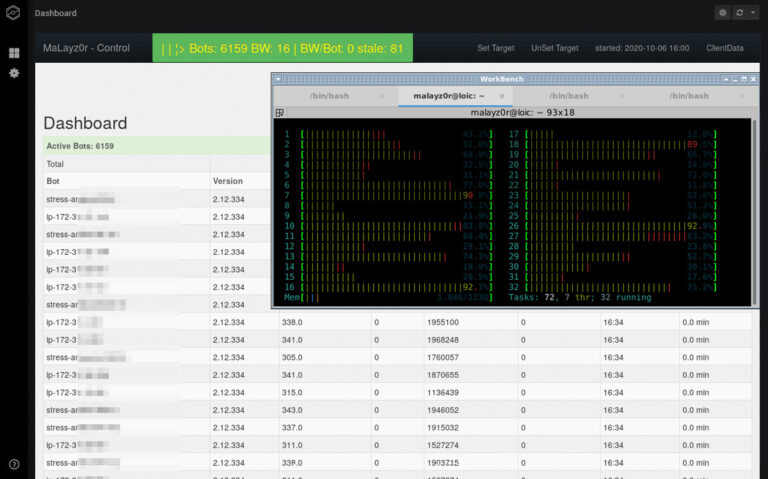
- Simulation of real botnets (server, IoT, Mirai etc)
- Completely customizable attacks
- Interactive dashboard: every attack is recorded and can be replayed for later analysis
- Multi-Location-Monitoring
References of our work
We have already successfully tested these manufacturers, technologies and providers, among others.
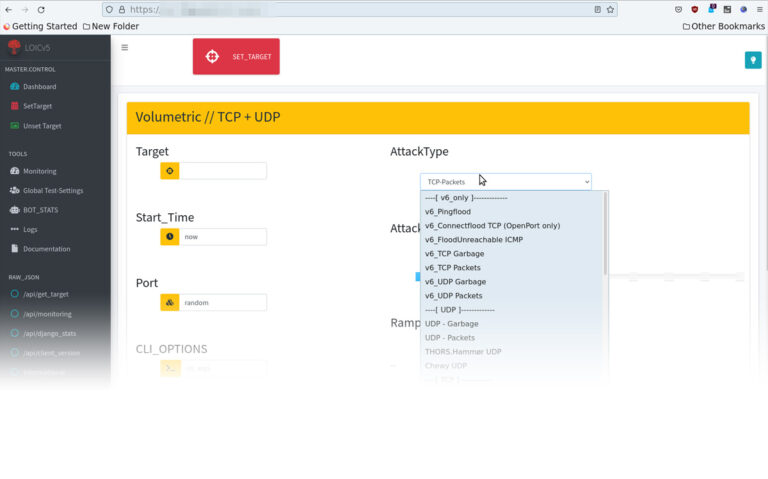
AttackModes
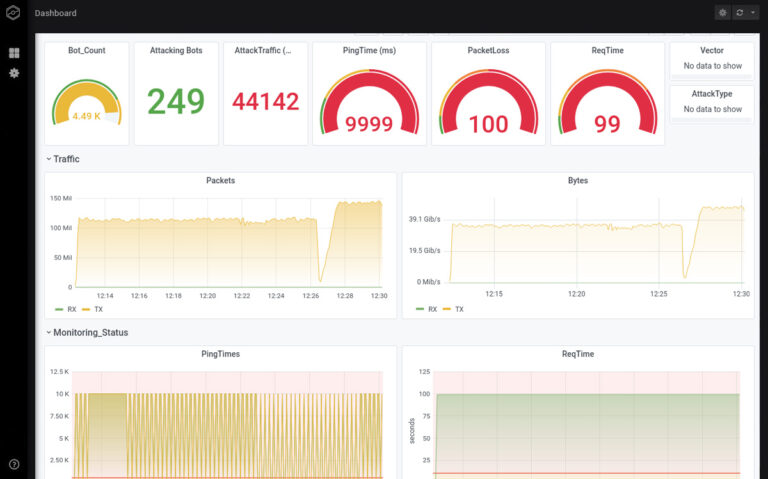
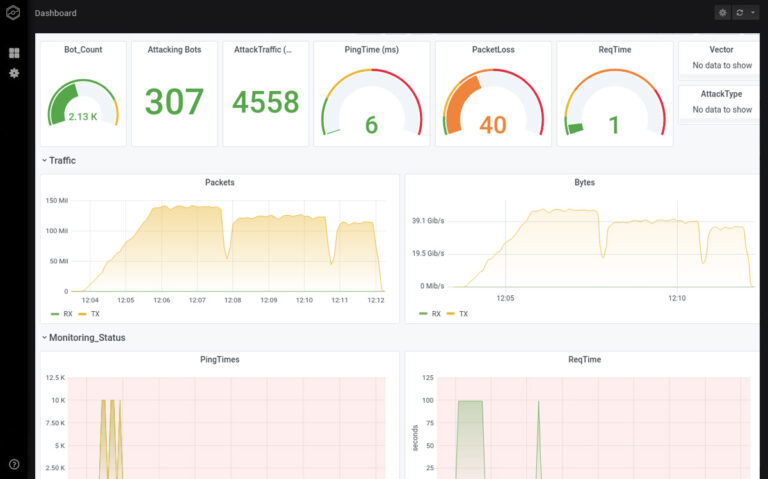
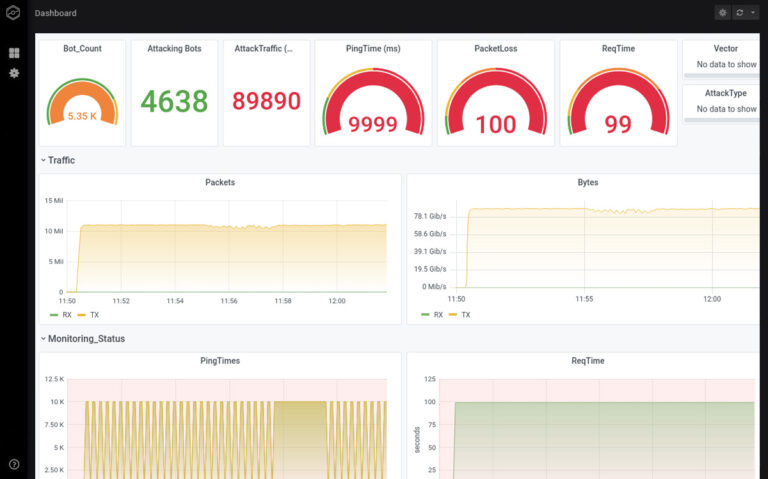
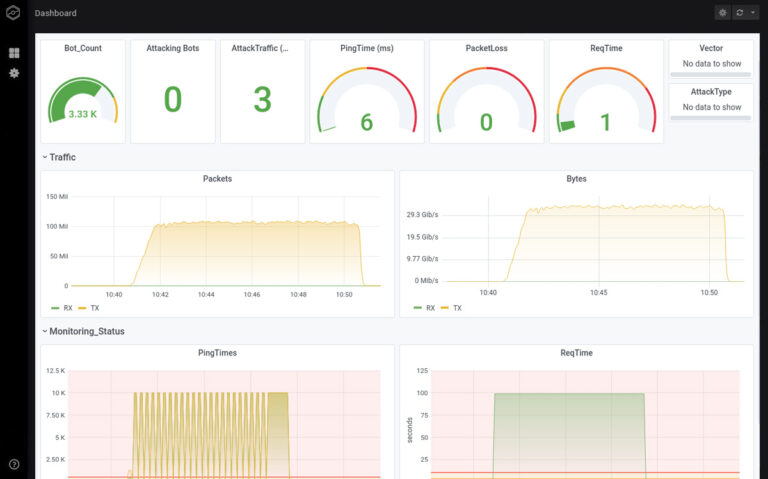
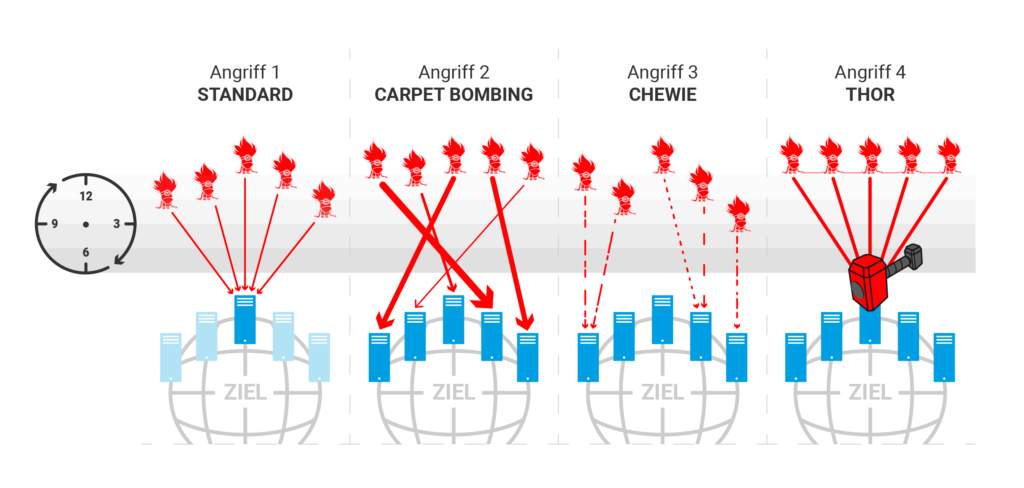
- Standard: Attack on individual IPs, ideal for proof of performance and night tests [image left, 1].
- CarpetBombing: Attack on entire networks, necessary for advanced proof of performance and increased threat levels [def. afterflg.].
- ChewieAttack: CarpetBombing v 2.0; each attacker IP only sends traffic for max. 30 seconds, then goes into standby and searches for a new target after 2 minutes [Def. afterflg.].
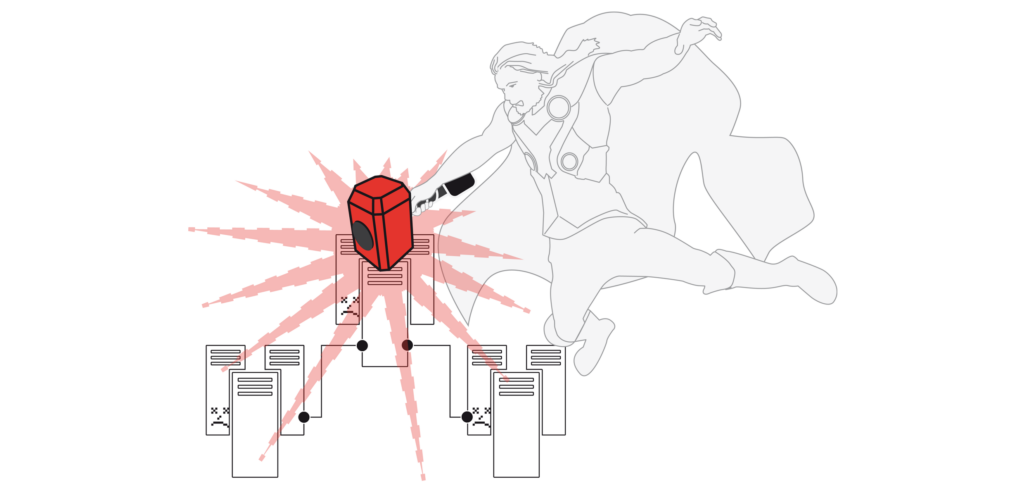
- Thor's hammer: attack tuned to the millisecond (Thor's hammer); an in-house development with resounding success [image right].
Carpet bombing attacks are a new variant of the more common reflection or flooding attacks, where instead of focusing the attack on a single destination, the attacker attacks every destination within a specific subnet or CIDR block (for example, a /20). This will both make it more difficult to detect the attack and also to mitigate it, potentially resulting in outages due to the flood of attack traffic across network devices and internal links.
In addition, these attacks are often fragmented, resulting in a flood of non-initial IP fragments, which can be tricky to mitigate. The attacker will often shift their attacks from one subnet (or CIDR block) to another, complicating the detection and mitigation even further.
Very similar to Carpetbombing in terms of target selection, the Chewie attack brings more randomness to the game by choosing target, strength, vector and protocol completely at random.
This ensures that pure statistics-based detection methods are completely confused, as the packet stream from an attack IP never lasts longer than 30 seconds, and then stops for at least 120 seconds, only to start again with a new target and pattern.
Although only 25% of the bots in a botnet are active at any one time, the attack is much more difficult to defend against
DDoS RedTeaming
We are able to both recreate and carry out sophisticated attacks. Target analysis and selection are carried out using the "Recon" and "OSINT" methods in order to subsequently identify the neuralgic points of interest.
... to test the defence and simulate a real "targeted attack"!
We have seen in several DFIR analyses that this attacker behaviour is not uncommon.
The links on the right take you to the detailed reports.
Scope
- Networks or applications
- Selected period (minimum 30 days)
Attack modules
- all attacks that can also be found in the targeted attacks section
- SmokeScreening
Target groups
- Vendors/protection providers
- Security teams with a high security level
*New load generators are used for all attacks to prevent "learning" of signatures.
Reasons for a stress test
- Proof of performance for the individual network components
- Check whether DDoS protection measures are working as desired (proof of function)
- Measure your own level of protection compared to the threat situation according to the DDoS Resiliency Score
- Test whether administrators are sufficiently trained for a DDoS attack
- Optimising the workflow in the event of a DDoS attack
- Assess the impact of a successful attack
- Assess the impact of a successful attack
The following targets can be tested:
- Networks
- BGP-Router
- Firewalls and VPN gateways
- Web server/web infrastructure
- APIs
- SSL Offloader
- Load balancer
- DNS-Infrastructure
- Any TCP services
- DDoS-Appliances
Attack vectors
- Layer 3/4 (volume attacks)
- Layer 7 (attacks on applications)
- IPv4 or IPv6
- Attacks against firewalls
- Attacks against load balancers
- DNS-waterboarding
- CDN-reflections
- Over 50 different types of attack in total
- custom attacks
- Real world botnet simulations (10,000 IPs)
- Paperworks and dry runs for emergency workflows